Lessons from the CrowdStrike incident
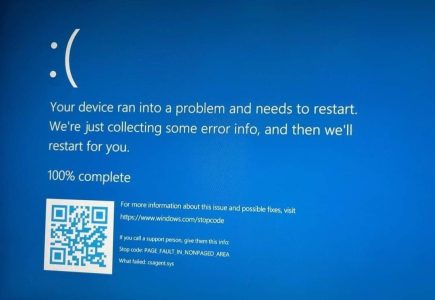
Yesterday, there was a world-wide incident that affected computers running CrowdStrike Falcon, where there was a conflict between the vendor’s anti-malware protection and the Windows sensor, resulting in a BSOD and unresponsive computers. This is a major incident that was effectively the effective impact as we were expecting from the… Continue Reading Lessons from the CrowdStrike incident