Password tips for ease of use
In our ever-increasingly online lives, passwords have become a vital part of our existence. However, passwords are still the most vulnerable part of our security – because they are created and used by people, who persistently are the weakest point in any security protection. Why are passwords so easy to get wrong, and what can we do about it? Here are my password tips for ease of use, to get easy passwords.
The threat vector has changed
In the 80’s, 90’s, and 2000’s – when we entered passwords, we needed to ensure that a ‘shoulder surfer’ could not see what we were typing. The advice was also to never write passwords down, in case someone near you could see what you had written. This advice was because systems were largely local and so people would need to be in the offices of a company to access their systems.
The world has changed to a hyper-connected Internet approach, where people are now getting rid of any local system, and everything is accessible over the Internet. That means the threat vector has changed to external actors – people who cannot see the Post-It note on your screen, because they have no idea (and don’t care) where you are.
Encryption vs Hashing
In the early days of corporate computing, passwords were stored in a Hash, which is a computational process where a user’s plain text password is converted into a scrambled version with a key that is unique to each system. The password is never actually stored, and the hash can’t be converted back into a password – however, if someone gets the key, they can generate hashes from new passwords, and compare the hashes. Hackers publish “rainbow tables” of known hash values and their associated passwords, meaning that in the current environment a hash is not secure.
Encryption is different, in that when a password is decrypted, it is either 0% decrypted, or 100% decrypted – there is no way of knowing if the attempted decryption is “close” – so attempts by hackers have to try every combination of passwords, and only know they have got it right when they get access to the system (or file).
Password complexity vs length
I encountered the below image, and there are many more like it on the Internet. They show how quickly a short and simple password can be broken by using brute-force guessing. The statistics are aiming to show that you can make your password longer to crack if you make it longer or more complex. These figures are based on how long it takes to try every single combination of letters, numbers, symbols etc. – so in reality a password would be cracked slightly quicker than these values below, unless the password is ZZZZZZZZZ (or the last possible combination).
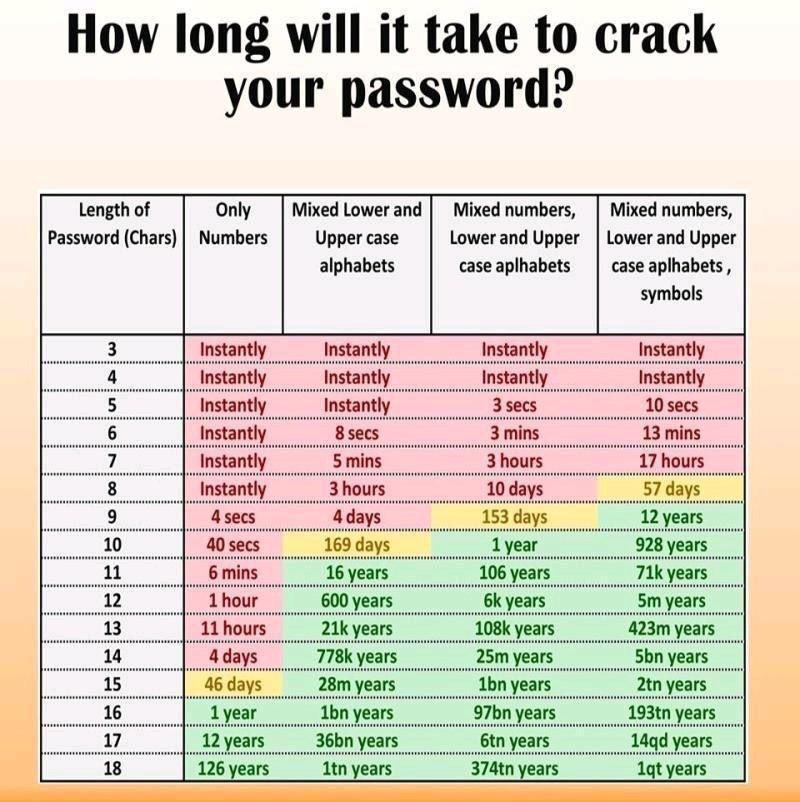
However, the interesting thing is the shape of this chart. It is not directly proportional between length and complexity. If you take the example of a 9 character password that is a mixture of uppercase and lowercase characters – changing one of the characters in the 9 character password will make it take [up to] 153 days to crack, however, just by adding one extra character (not a number or a symbol), this improves to [up to] 169 days. If you look at a 10 character password, this simple change makes the ease of cracking change from 1 year to 16 years. So, this shows that password length is a quicker and easier way to improve security.
Easy Passwords

A password has to be easy to use – because a person needs to type it in. We have all seen auto-generated passwords that are complex random mixtures of characters – 7y%QYc/hS#@b is an example. This 12 character password will, according to the chart above, take [up to] 5 million years to crack. However, can you remember, or even type, the suggested password. The words ChallengingBit is 14 characters long, and according to the chart above will take [up to] 25 million years to crack. Which one do you remember? Which one can you type quickly? Which one could you verbally tell someone else – if needed?
Many people recommend password manager tools to store and recall the complex passwords – which is great, but it is not perfect. Both LastPass and others have been hacked, and they depend upon a master password – one key to rule them all.
Secure, and easy to use passwords

We all need to increase the security of our passwords. Yes, we can substitute special characters such as P@s5w0rd – but this is not more secure than making it longer such as PasswordH, it just makes it more difficult to type and remember. What we really need to do is make the passwords long! However, many systems insist on ‘complex’ passwords, and will not accept a long and secure password that does not contain the characters.
Instead, I recommend a scheme to help you remember your password, and to keep it both secure and unique. Many people use the same password for multiple services, because that is easy for them to remember and type – but with this scheme you can keep the poor password, just make it better.
In this scenario, ‘your’ frequently used and bad password is the word password. The service you want to use is Facebook. Here are some passwords that will be secure, easy to remember, and long!
- passwordFacebook
- password4Facebook
- FacebookPassword
- password(Facebook)
- password#Facebook
- My#1Facebook-Password
- ThisIsMyFacebook_Password
By adding the site name to your existing bad password, you make the new password more secure, remind yourself what it is for, and can also meet complexity requirements. However, the ones above are a bit too easy to guess, so be a bit more cryptic…
- password4BlueSite!
- Pass&word-social8
- password4F-pages
You get the idea – keep with what you know and will remember and type correctly, but make it longer instead of more complex – you can put in special characters or numbers between words if the site demands it.
Fighting the haters
I know I will get a lot of hate from security experts that tell us to not use dictionary words, have cryptic and complex passwords – but the undeniable truth is that the weakest point in any security is the humans who use it. Making the passwords longer makes them more secure. Making passwords memorable and easy to type makes them more usable.
This is another approach that has had many haters – but I agree with it;

We all want easy passwords that are also secure – if this article tells you nothing more than to come up with unique passwords for every site that are easy and LONG, then I have succeeded.