Obvious PCI-DSS benefits
Last month, I wrote an article on the Essential 8. The article pointed out that for most of the measures, they should be the absolute minimum measures that organisations take with their systems. For those who work in the area of security, most of the Essential 8 are common-sense and obvious, and many professionals would not allow their environment to not cover them. There are many other frameworks and mitigation strategies that guide IT and cybersecurity professionals, and today I want to focus on obvious PCI-DSS benefits from the standard. The framework for the Payment Card Industry Data Security Standard is a set of standards that is intended to protect credit card and financial information, but if you change a few words, then it can apply to most industries. The standards can apply to other industries and organisations, even those who don’t handle credit card information, as there are obvious PCI DSS benefits for how data is handled for cybersecurity.
History of PCI DSS
Even though PCI DSS was created by Mastercard, Visa, American Express and the other cards of Discover and JCB, it is a set of standards that apply to any important data that must be kept secure. The standard was created in 2004, and there are four levels of compliance that vary depending upon the number of credit card transactions. The standard is regularly reviewed and updated, and is currently in it’s fourth major iteration.
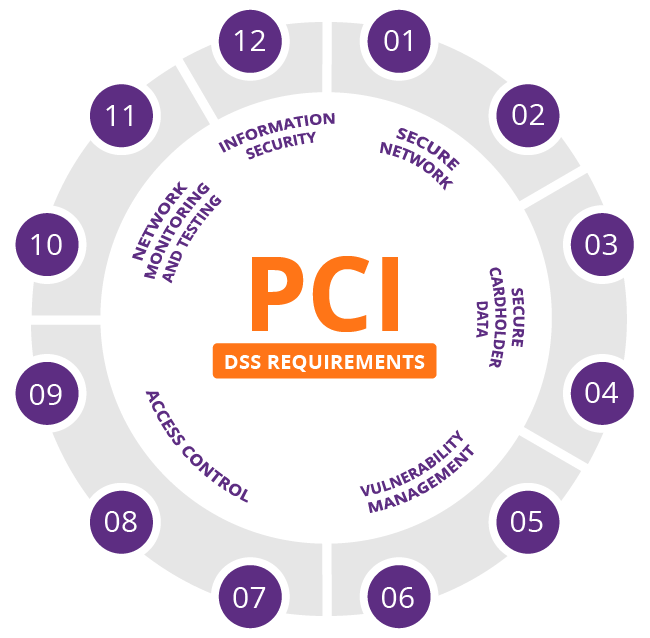
The 12 standards of PCI DSS
There are 6 areas of compliance, and 12 standards. If you take the words “cardholder data” and replace them with “critical data”, these 12 standards can be applied to any business that wants to take security seriously, even if they don’t handle credit card information.
The 12 requirements of PCI DSS are:
- Install and maintain a firewall configuration to protect
cardholderdata - Do not use vendor-supplied defaults for system passwords and other security parameters
- Protect stored
cardholderdata - Encrypt transmission of
cardholderdata across open, public networks - Use and regularly update anti-virus software or programs
- Develop and maintain secure systems and applications
- Restrict access to
cardholderdata by business need to know - Assign a unique ID to each person with computer access
- Restrict physical access to
cardholderdata - Track and monitor all access to network resources and
cardholderdata - Regularly test security systems and processes
- Maintain a policy that addresses information security for all personnel
Common-sense approaches
The above list of 12 requirements should seem logical and common sense. Nothing too strange or weird, right? Obvious that you should have a firewall, not to keep the default passwords, use encryption when in open networks, and have anti-malware software. These all seem like the most obvious and common sense things to do.
The next few measures are more specific, and so your mileage may vary with your implementation and use of these standards. Developing secure systems and applications can be re-interpreted as “select” secure systems. Restricting access to those who need to know will be something that any company with an HR or finance department already does, and assigning a unique ID means to not have generic usernames where you don’t know who is doing what. Physical access to data is less likely when using cloud, and keeping logs of all access seems easy (but it often isn’t!). The final two of testing security and procedures, and having policies in place are also a no-brainer – particularly when your organisation reaches a size where you have departments and have grown to need written policies.
Applicability for any business
Like all the best standards and frameworks, these measures make sense and don’t seem like unusual requirements and requests. Taking the PCI-DSS standard as recommendations for any business will be a great step towards improving your organisation’s security.
