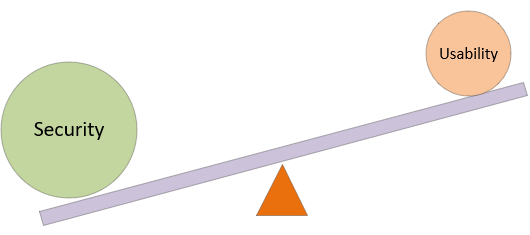
Challenging the balance between security and usability
It is a well-known adage in cybersecurity that there is a balance between usability and security – if you increase the security and control, you decrease usability. Conversely, to make a system user-friendly and easy to use, it has to be done at the cost of lowering security. This has… Continue Reading Challenging the balance between security and usability