Things not to do in security
Security is more than just activating firewalls and having complex passwords – it is a culture and an approach. There are many things that we are told to do, but also what is important is what not to do in security. Here is my list of the top 5 things to not do in security.
Your signature
For centuries, scribbling your name in an unusual way was considered to be a secure way of identifying yourself. As a child or a teenager, you make a decision to write your name in some sort of scribble, and then we stick with it all through our lives. We use it on cheques (checks), documents and credit cards – but it is not really that secure. The problem is that every example of your signature is an example to copy. One way to make it even easier to copy is to put an electronic image of it into documents or emails. Even though your “wet” signature is not effective as a security method, don’t give people a pristine digital version to re-use.
ID cards, keychains and business cards
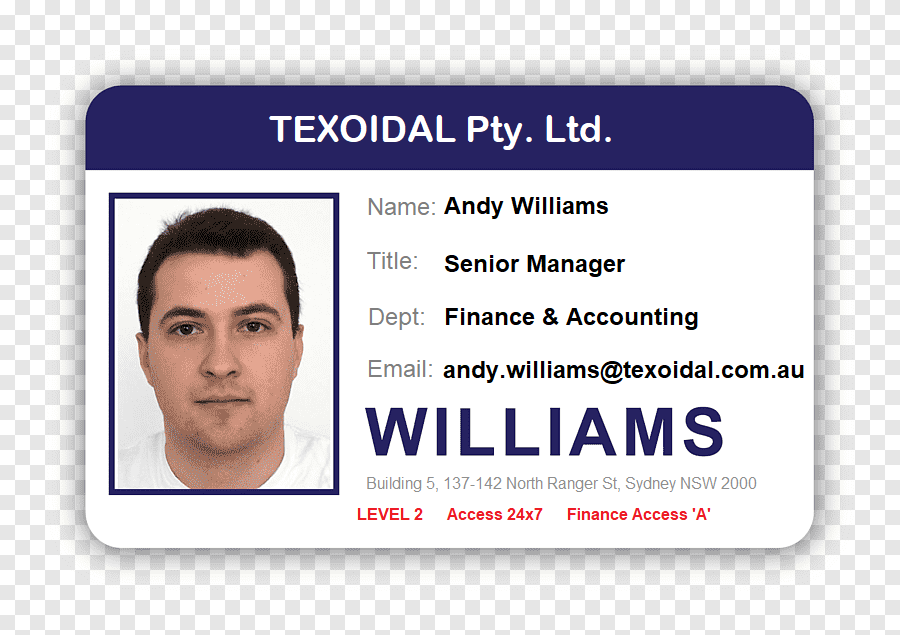
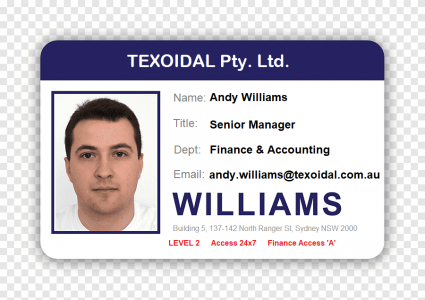
Don’t publish all your information for everyone to see. If you have a building pass, particularly if it is a proximity card key itself, this can be a big security vulnerability. Would you put your home address on your house keys? So, if you drop it or leave it somewhere, the key tells someone what is unlocked by those keys. The same with office building passes – don’t put the building address on the card. You should not have your photo on the card either, as it informs someone what they need to look like in order to get access. The same with a department name or job title – this informs someone who finds or steals the card on what areas they can get to. I also think it is bad to put even a name on the access card, particularly if it is normally worn on a neck lanyard on hanging off a belt – it gives someone information about you. Someone could approach you, saying “Hey, it’s John, isn’t it? Are you still in Accounts? Can you help me in the building because I left my pass at home…”
Business Cards (or name cards) can also be a security risk of information disclosure, where all your contact information is presented all together at once. Whilst you want a business contact to have that information, you don’t want your contact numbers (which now will be your personal mobile number / cell number, instead of an office direct line), or your email address disclosed. When an email format is known, it gives an attacker more information for not just you, but also others in your company – an attacker now knows the format is [email protected], so they can go to LinkedIn and now spoof an email from your boss.
Default or physical passwords
It may be the simple way to operate – particularly for older people or in instances where a device needs to be frequently factory-reset to the defaults, but don’t leave the default password on your devices. It may look like the password is a random bunch of characters, but these passwords are known. Change your default passwords (if you must, just add a new word to the end to make it longer), but never leave it on the same password that was supplied.

When it comes to PIN locks, these can get worn and reveal the numbers that are needed – the attacker just needs the order as they have the numbers. Ensure that you change these combinations, a good time to do so is when someone leaves the company, or you change suppliers (cleaners, particularly – see below).
Don’t reveal too much
An attacker may not know anything about you – sometimes not even your company name or country. You want to keep that balance on your side – don’t reveal too much. This includes things like declaring your password requirements – stating that you need a minimum 8 character password with uppercase and numbers and symbols may seem like a good idea, but it means an attacker can reduce the combinations of passwords to try. Seeing your password requirements means they can ignore all attempts to use 7 character lowercase only passwords.

If you really have to post a selfie at your desk, or a snap of your server room, or the reception desk at your new offices – be aware that a malicious actor will be examining everything about the photo to gather more information. Even the model of your laptop or printer could be used as a vector to send you phishing emails with malware payloads, or the physical size of a corridor between two cabinets will give them additional information they may need.
Don’t blindly trust
Your suppliers need to be vetted to ensure they are secure – but also to ensure that there is ongoing evaluation and investigation. If you have cleaners who have keys to your building at night, unsupervised, don’t just take the brochure of the company that says all cleaners have a police check – ask for proof that it has been done regularly (annually, at least – ideally more regularly). Don’t forget your landlord – as they have keys too! You may have suppliers who provide a fully hosted service, but have their staff been checked to see if they have recently been convicted of a crime, and how frequently do they audit their own suppliers? Supply chain risk can sneak up on you if you don’t keep checking it – staff move and people do stuff in their lives, and all of it could affect you!
How to out-run a lion

There is an old joke – how do you run faster than a lion? You don’t have to, just outrun the slowest person in the group! This is largely similar for most cybersecurity concerns – the hackers and cybercriminals are looking for the easy wins, the slow and weak who make obvious mistakes. Just changing your default passwords and configuration, following industry standard advice (like the Essential 8) and being even a bit diligent will put you one step ahead of the easy victims.
I have often said that cloud security is much better than any security you could do yourself, however it is very easy to make a mistake and configure it to be fully open and have no security at all – and you would not find out until you suffer an incident. Check your configuration, document your settings, and regularly check that no settings have been changed to allow the lions in (or that a persistent threat has not reconfigured your settings).